Smart Contract Security: Common Vulnerabilities and Their Lasting Presence
Smart contracts have revolutionized industries by automating transactions on blockchain networks without intermediaries. Despite their transformative potential, smart contracts remain prone to various vulnerabilities that continue to compromise their security. Even after high-profile hacks and extensive research into smart contract security, these vulnerabilities persist. This article outlines these common security issues, categorizing them into three major groups: Unsafe External Calls, Usage of Spot-Price, and Authentication Issues, while also addressing the increasing threat of Phishing Attacks in Web3.
Common Vulnerabilities in Smart Contracts
| Vulnerability Type | Attack Type | Example |
|---|---|---|
| 1. Unsafe External Calls | Reentrancy Attack | The DAO hack of 2016 |
| Uninitialized Proxy Bug | Misconfigurations in upgradeable contracts | |
| 2. Usage of Spot-Price | Price Oracle Manipulation | Flash loan attacks |
| Flash Loan Attacks | Exploiting price discrepancies | |
| 3. Authentication Issues | Poor Access Control | The Bancor Hack of 2018 |
| Delegatecall Vulnerabilities | The Parity Multisig Wallet Hack of 2017 | |
| 4. Phishing Attacks | Impersonation | Fake "airdrops" or "free token" offers |
| 5. Additional Vulnerabilities | Gas Limit Attacks | Manipulating gas limits to force contract failure |
| Integer Overflow and Underflow | Errors due to exceeding data type limits | |
| Front-running Attacks | Executing transactions ahead of legitimate ones | |
| Social Engineering Attacks | Tricking users into revealing sensitive information |
1. Unsafe External Calls
Smart contracts sometimes need to interact with other contracts or addresses, which can lead to risks if not handled safely.
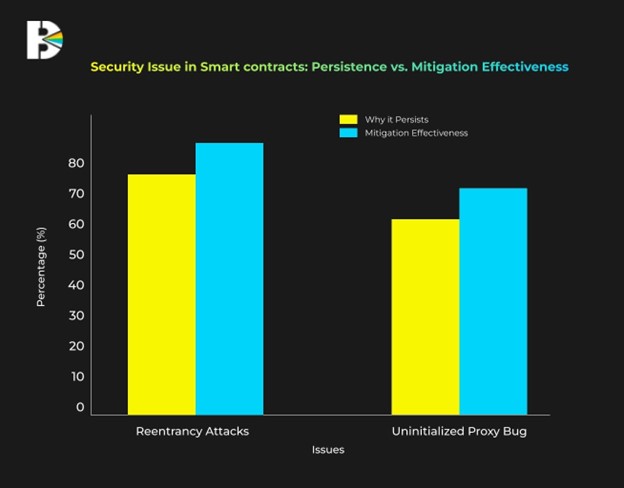
Reentrancy Attacks
A common example of unsafe external calls is the Reentrancy Attack. This happens when a contract calls an external function, and before that call finishes, the external contract calls back into the original contract. This allows the attacker to take advantage of the contract’s functions and drain its funds.
- Example: In the DAO hack of 2016, over $50 million worth of Ether was stolen by exploiting this vulnerability.
- How to Prevent It:
- Use the Checks-Effects-Interactions pattern to update the contract’s state before making external calls.
- Add a reentrancy guard to prevent recursive calls.
Uninitialized Proxy Bug
In upgradeable contracts, if the proxy isn’t properly set up during deployment, it can create security holes.
- Why It Happens: Mistakes during setup or insufficient testing can lead to this vulnerability.
- How to Prevent It:
- Always initialize proxies during deployment.
- Perform regular audits on upgradeable contracts.
2. Usage of Spot-Price
Some smart contracts depend on real-time asset prices, called spot prices. These prices can be manipulated by attackers if they aren't sourced properly, leading to vulnerabilities.
Price Oracle Manipulation
In DeFi, protocols use price oracles for real-time data. If an oracle is compromised, attackers can exploit inaccurate data to drain funds.
- How to Prevent It:
- Use decentralized oracles that collect data from multiple sources.
- Cross-check data for accuracy before using it in contracts.
Flash Loan Attacks
Flash loans allow attackers to borrow large amounts of money without collateral and manipulate prices temporarily.
- How to Prevent It:
- Implement slippage controls to limit price changes in one transaction.
- Use tamper-resistant price feeds to mitigate risks.
3. Authentication Issues
Smart contracts often have problems with access control and authentication, leading to unauthorized access and malicious activities.
Poor Access Control
This occurs when functions that should be restricted are left open to everyone. If critical functions are not properly protected, it can lead to unauthorized people accessing them, potentially resulting in theft or mismanagement of funds.
- Example: In the Bancor Hack of 2018, poor access control allowed attackers to steal funds.
- Mitigation:
- Implement Role-Based Access Control (RBAC) to assign permissions based on user roles.
- Use smart contract features like the onlyOwner modifier to ensure that only authorized users can access sensitive functions.
Delegatecall Vulnerabilities
The delegate call function allows one contract to run the code of another contract but use its own storage and data. If misused, it can lead to the manipulation of the contract’s internal state by unauthorized parties.
- Example: In the Parity Multisig Wallet Hack of 2017, an attacker exploited this vulnerability.
- Mitigation:
- Avoid using delegatecall unless necessary, and review the logic of contracts being called with delegatecall.
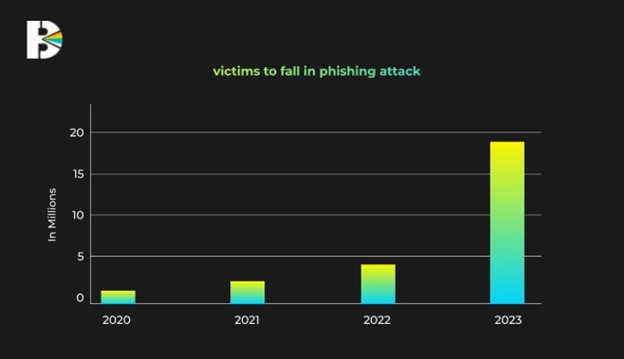
4. Phishing Attacks in 2024: A Year of Evolving Threats
2024 has seen a significant increase in phishing attacks, using more sophisticated techniques and targeting a wider range of victims.
Key Trends in 2024 Phishing Attacks
- Increased Use of AI: Phishers leverage AI to generate convincing phishing emails and messages.
- Targeting of Businesses: Attackers focus on compromising sensitive company data.
- Rise of Smishing: SMS phishing attacks have grown more prevalent.
Mitigation Strategies
- Stay Informed: Keep up-to-date with the latest phishing trends.
- Verify Information: Always verify emails and links before clicking.
- Use Strong Passwords: Create complex passwords and enable two-factor authentication.
Be Cautious of Urgent Messages
Phishers often try to create a sense of urgency to pressure victims into acting quickly.
Report Phishing Attempts
If you encounter a phishing attempt, report it to the relevant authorities and the platform or service being impersonated.
By understanding the evolving landscape of phishing attacks and taking proactive measures, you can significantly reduce your risk of falling victim to these scams.
5. Additional Vulnerabilities to Consider
- Gas Limit Attacks: Attackers can manipulate gas limits to force smart contracts to fail or behave unexpectedly.
Mitigation: Limit gas usage and consider fallback mechanisms when gas limits are exceeded. - Integer Overflow and Underflow: These errors occur when numbers exceed the limits of the data type.
Mitigation: Use safe math libraries to prevent overflows and underflows. - Front-running Attacks: Attackers observe pending transactions and execute their own transactions before legitimate ones.
Mitigation: Use decentralized order books and private transaction pools. - Social Engineering Attacks: Attackers may impersonate trusted individuals or partners to trick users into revealing sensitive information.
Mitigation: Implement multi-factor authentication (MFA) and educate users on social engineering threats.
Why These Vulnerabilities Persist
- Complexity of Systems: The decentralized nature of blockchain makes comprehensive security difficult.
- Rapid Innovation: The fast-paced evolution of Web3 and DeFi protocols means new vulnerabilities continuously emerge before old ones are fully addressed.
Conclusion
Smart contract and Web3 vulnerabilities, such as reentrancy attacks and phishing scams, remain significant risks. Developers must follow best practices like proper access control, secure price feeds, and regular audits, while educating users on security. Ongoing improvements are essential to ensure the safety and trustworthiness of decentralized systems.




